[ad_1]
Critical Infrastructure Security
Lack of Money, Expertise Creates Big Challenges For Small Infrastructure Providers
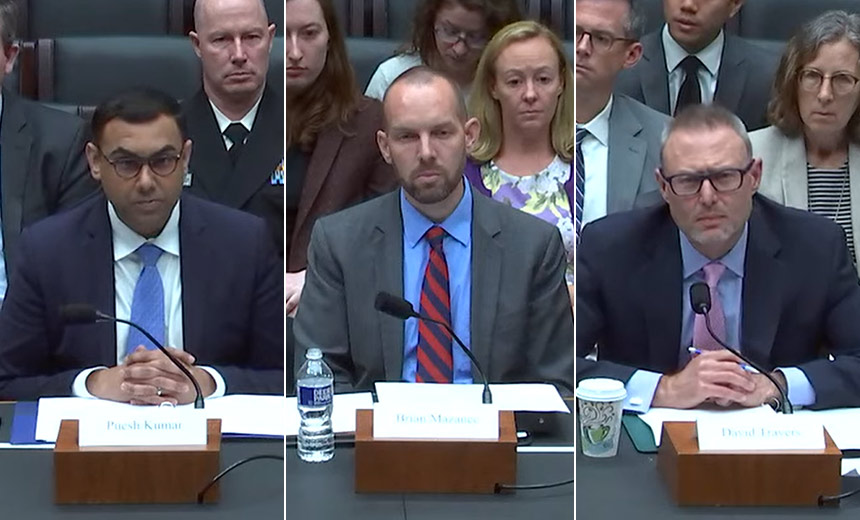
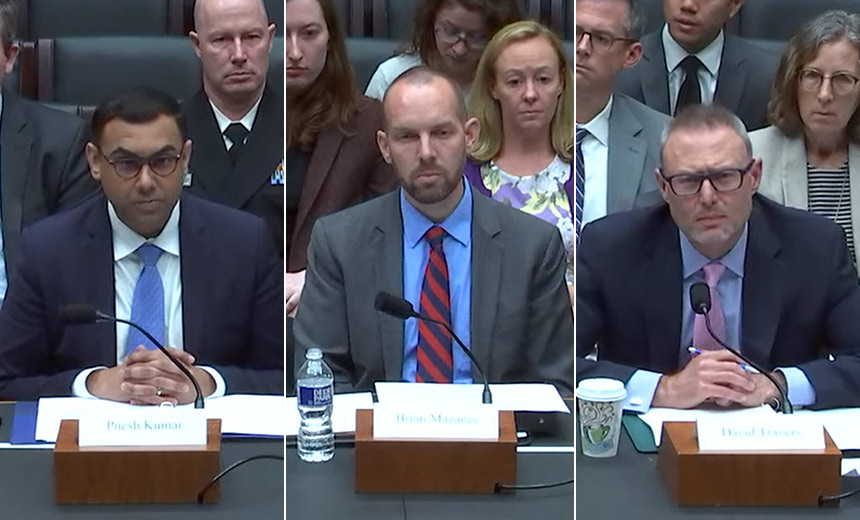
Small electric utilities, wastewater facilities and hospitals struggle with defending their organizations against emerging cyber threats given their meager resources, U.S. government officials told a congressional oversight panel Tuesday.
See Also: OnDemand | Attack Surface Management 2.0: Leveraging Vulnerability Analytics & Threat Intelligence
Slightly fewer than 100,000 drinking water systems and 16,000 wastewater systems serve the United States and its territories, with customer bases ranging in size from more than eight million to just 500 people, said David Travers, head of the Environmental Protection Agency’s Water Infrastructure and Cyber Resilience Division.
“The most significant cyber risk in the water sector remains the failure of many utilities to adopt best practices,” Travers said. “This critical vulnerabilities is apparent both from a recent industry survey – which showed that most utilities had not taken key steps to protect their operation – and from cyber incidents at water systems, which have exploited the failure to implement cybersecurity best practices.”
Travers testified before a House Energy and Commerce subcommittee panel alongside Puesh Kumar of the Energy Department and Brian Mazanec of the Health and Human Services Department.
The EPA has provided one-on-one technical assistance to hundreds of smaller water and wastewater systems, with subject matter experts identifying gaps in cybersecurity best practices and implementing remediation actions tailored to the resources and goals of the utility entities. The agency in March said it will start assessing cybersecurity as a factor in periodic safety assessments (see: US EPA Regulates Public Drinking Water for Cybersecurity).
“These systems, though small, are critical to the viability of the communities they serve,” Travers said. Their smallness often puts them at greater risk since they lack the dedicated cybersecurity personnel of larger systems, he told lawmakers.
The EPA focuses on best practices such as strong and unique passwords rather recommending resource-intensive interventions. Travers said the EPA also offers ‘train the trainer’ programs to third parties like the National Rural Water Association and the Agriculture Department’s Rural Community Assistance Program, who often serve as a source of technical expertise.
The Energy Department provides tools to smaller utilities that help them both gauge their existing cyber posture and make investment decisions, said Kumar, director of the Office of Cybersecurity, Energy Security, and Emergency Response. The department’s rural and municipal utility grant program delivers cybersecurity technical assistance and funding right to rural cooperatives and waste utilities nationwide.
Why Incidents At Small Hospitals Are More Severe
The Health and Human Services Department has developed separate sets of industry best practices for small, medium and large hospital systems with off-the-shelf resources that small hospitals can use as is, said Mazanec, deputy director for the Office of Preparedness.
“Our focus is on safety and health impacts for smaller, rural hospitals located in an area where there aren’t multiple hospitals and less ability to divert when there is a need,” Mazanec said. “In some respects, that can make the incidents even more severe when they do occur, in addition to the fact that they may have less resources to harden their target.”
In response to this bifurcation, Mazanec said HHS has developed tailored resources that will make it easier and more efficient for smaller, less resourced hospitals to harden their infrastructure. In addition to off-the-shelf tools, the agency offers an “on-demand” series of courses to help small institutions that lack resident cyber experts and will collect data on how existing tools are used to drive future revisions.
“We engage closely with the sector, we coordinate with them, and we’re developing tailored tools,” Mazanec said. “This is also why we think we need to elevate our activity. The threat is growing.”
[ad_2]
Source link