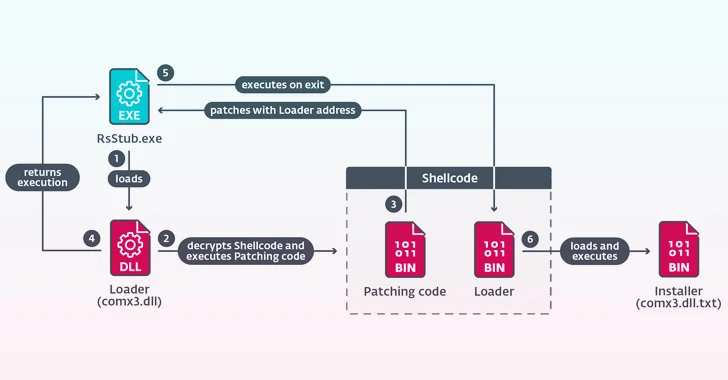
Critical Jenkins Vulnerability Exposes Servers to RCE Attacks
[ad_1] Jan 25, 2024NewsroomVulnerability / Software Security The maintainers of the open-source continuous integration/continuous delivery…
0 Comments