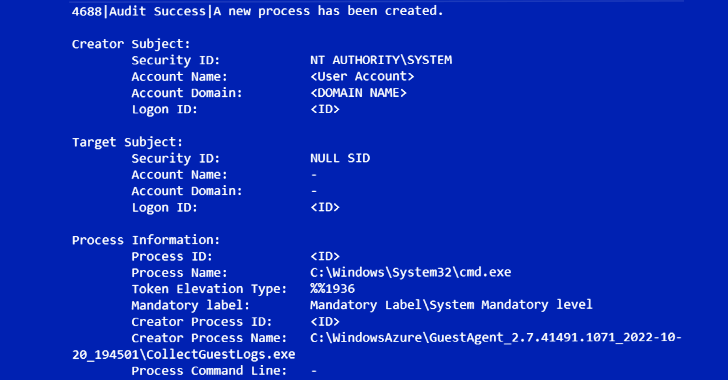
8220 Gang Exploiting Oracle WebLogic Flaw to Hijack Servers and Mine Cryptocurrency
[ad_1] May 18, 2023Ravie LakshmananCryptocurrency / Server Security The notorious cryptojacking group tracked as 8220…
0 Comments