[ad_1]

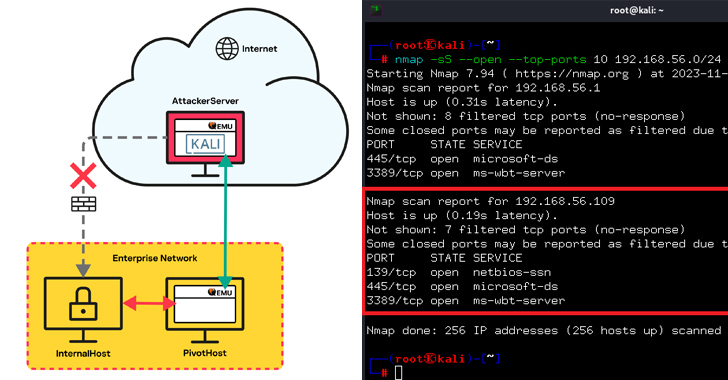
Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling software during a cyber attack targeting an unnamed “large company” to connect to their infrastructure.
While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to their advantage, the development marks the first QEMU that has been
[ad_2]
Source link
Categories:
bestiptvireland
certainly like your website but you need to take a look at the spelling on quite a few of your posts Many of them are rife with spelling problems and I find it very troublesome to inform the reality nevertheless I will definitely come back again